Description of GandCrab ransomware
Given the fast growth of the cryptojacking market, some big cybercriminal groups appear to have abandoned ransomware
distribution activity in favor of the more profitable foul play.
Under the circumstances, the emergence of a new competently crafted
sample of blackmail MalWarrior is quite an event.
That is the case with GandCrab, a ransomware strain boasting ramified
propagation routine and flawless encryption practices.
The GandCrab infection is making the rounds via several vectors. One involves exploit kits, that is,
malicious code exploiting software vulnerabilities on target computers after
would-be victims visit a compromised website. The kits leveraged in this particular campaign include RIG and GrandSoft.
Another way of depositing the malicious program onto systems
revolves around spam. In this scenario, users receive emails disguised as invoices that contain toxic attachments.
Simply opening the attached file suffices to unknowingly launch a harmful
PowerShell script that downloads ransomware modules proper.
A peculiar hallmark of GandCrab is its use of the .bit top-level domain for communication with its C2 servers.
This tactic allows the culprit to fly under the radar of some security
solutions installed on compromised PCs. Once the ransomware has scanned the host for potentially important data and
obtained a public encryption key from its Command & Control server,
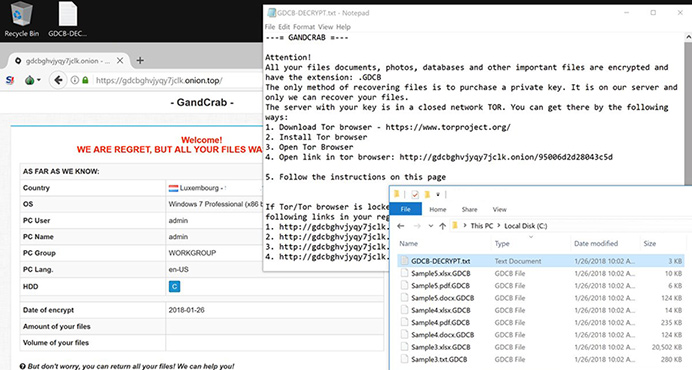
it encrypts those files using RSA cryptographic algorithm. It also concatenates the .GDCB extension to filenames and
leaves a ransom notification named GDCB-DECRYPT.txt. Ultimately,
the victim is coerced to visit the GandCrab Decryptor page that instructs them to submit 1.54 Dash worth some $1,200.
Dash is a form of cryptocurrency that’s used by ransomware
peddlers for the first time.
Security experts advise against submitting the ransom to cybercrooks.
Instead, those infected should try alternative ways of data recovery through backups, Shadow Copy service and forensic software.
GandCrab ransomware attack screenshot
About Adware Away and Customizing Removal Service
Adware Away is the only product that doesn't provide free trial vesion in anti-malware industry. We have 100% confidence to remove any malware with Adware Away and its customizing removal service. The download link is to download a scan-only version, you are required to purchase it before using it to remove the malware it finds.


Customizing removal to remove any malware related to GandCrab ransomware
If the above automatical method doesn't work, you can request a customizing removal service to let us help you remove this new variant manually, just follow the steps below:
- 1. Launch Adware Away.
- 2. Click "Customizing Removal" tab.
- 3. Click "Diagnostic Scan" button and wait for the scan completes.
- 4. Send us the scan log file.
- 5. Our technical support will analyze your log file and send you back a removal guide file
- 6. When you receive the removal guide file, just drag and drop it into Adware Away window, the removal to the new variant will be done.
